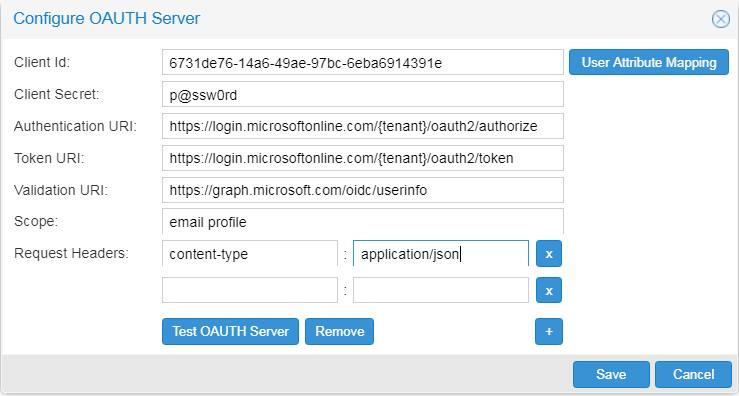
Configuring the OAuth server with Microsoft Azure Active Directory Web API
In this example, the authorization server is
Azure Active Directory (Azure AD) Web API.
Before you begin
- As an administrator, you have obtained OAuth 2.0 client credentials from the authorization server.
- As an administrator, you have configured the authorization server.
- You have been assigned a global role with the Security Administration capability.
Procedure
Results
Did this page help you?
If you find any issues with this page or its content – a typo, a missing step, or a technical error – let us know how we can improve!