Signature functional architecture
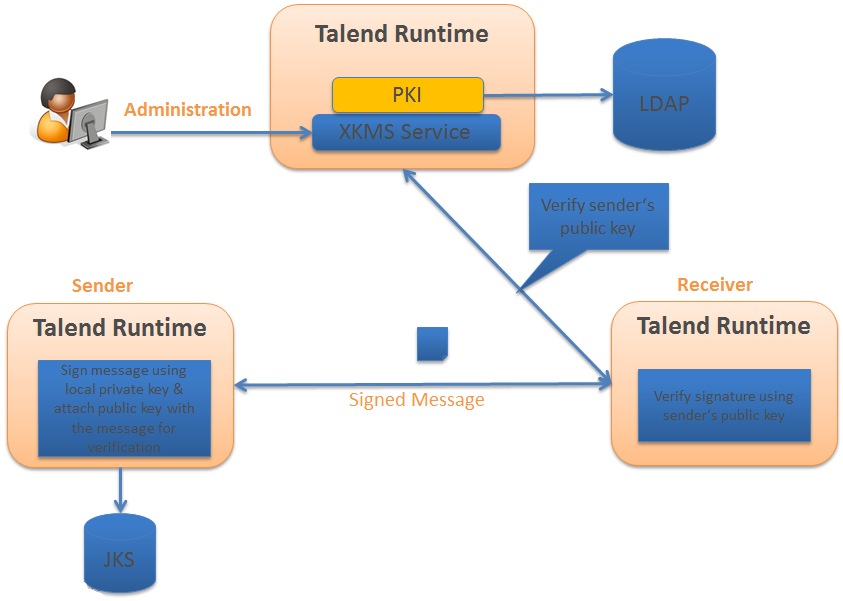
To send encrypted data to a receiver, senders encrypt the data with their own certificate (they sign the data). This way, the data are sent to the receiver associated with their own public key.
The receiver receives the signed data, validate that the public key is in the XKMS repository, and if the public key is valid, the receiver will be able to access the data.
Did this page help you?
If you find any issues with this page or its content – a typo, a missing step, or a technical error – let us know how we can improve!
