Detecting the fixed vulnerabilities (CVEs) of your artifacts while building
When using CI to build artifacts in big projects, you may want to detect which artifacts (Standard Jobs, Big Data Jobs, Routes) affected by Common Vulnerabilities and Exposures (CVEs) have been fixed since the latest Talend Studio update has been released.
- The option that allows you to detect fixed CVEs and report them in a file is available from org.talend.ci:builder-maven-plugin version 8.0.3 onwards (available from R2022-03). The detection of fixed CVEs for Route artifacts is supported from R2022-05.
- This option is aimed at helping users identify which CVEs might be fixed by a Talend Studio upgrade, and is not intended as a replacement for a third-party tool to find vulnerabilities in Talend Studio Job libraries.
Due to technical limitation:
- The CVEs for the jars used by Talend Studio but not by any component cannot be detected.
- The CVEs for the artifacts built as OSGI Bundle or Microservice in the report are not accurate.
Building the CVE report
Here is an example of command to build a list of artifacts affected by the CVEs. This command can be executed before or after generating the POM files of your project artifacts.
# To generate a report file listing all CVEs
mvn org.talend.ci:builder-maven-plugin:8.0.3:detectCVE
-Dgeneration.type=local
-Dproduct.path=/home/talend/talend_studio
-Dlicense.path=/home/talend/talend_studio/license
-Dproduct.path=/home/talend/talend_studio/commandline/Talend-Studio-YYYYMMDD_1234-V8.0.X/
<!-- This parameter is only supported and needed for users with Talend Studio 8.0.1 R2024-04 or lower
-Dtalend.studio.p2.base=https://update.talend.com/Studio/8/base -->
-Dtalend.studio.p2.update=https://update.talend.com/Studio/8/updates/R2022-03
-Dworkspace=/home/talend/talend_studio/CI/workspace
-DcveReportFilePath=/home/talend/talend_studio/CI/cvereport.csv
-s /home/talend/talend_studio/maven_user_settings.xml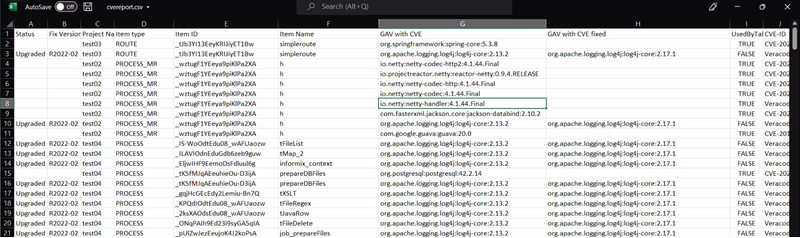
Analyzing the CVE report
| Column name | Definition |
|---|---|
| Status | Can be:
|
| Fix Version | The update version when the CVE has been fixed. Example: R2022-03 |
| Project Name | Name of the project impacted by the Common Vulnerabilities and
Exposures. Example: CI_PROJECT |
| Item type | Type of the artifact impacted by the Common Vulnerabilities and
Exposures. Example: PROCESS |
| Item ID | Identifier of the artifact impacted by the Common Vulnerabilities and
Exposures. Example: _GXOmQFizEeiOq-rLS_Z-8g |
| Item Name | Display name of the artifact impacted by the Common Vulnerabilities
and Exposures. Example: MyVeryComplexJob |
| GAV with CVE | The Maven Group, Artifact, Version (GAV) of the JAR file that has
unsolved vulnerabilities. Example: org.apache.logging.log4j:log4j-core:2.13.2 |
| GAV with CVE mitigated | The Maven Group, Artifact, Version (GAV) of the JAR file that has
fixed vulnerabilities. Example: org.apache.logging.log4j:log4j-core:2.17.1 |
| UsedByTalendComponent | Can be:
|
| CVE-ID | Identifier of the Common Vulnerabilities and Exposures. If not
available, you will get CVE-NOT_DISCLOSED. Example: CVE-2021-44228 |
| CVSS | The CVSS (Common Vulnerability Scoring System) score for rating the severity of security vulnerabilities in software. It can be between 0.0 and 10.0, with 10.0 being the most severe. For more information about CVSS, see https://nvd.nist.gov/vuln-metrics/cvss. |
| Component Names | Name of the component impacted by the Common Vulnerabilities and Exposures. It can be the technical name used for code generation, or it can be studio if it impacts the whole Talend Studio. |
| Comment | Additional comments. |
Indicating from which Talend Studio update version to build the CVE list
Here is an example of command to build a list of the fixed CVEs detected from version R2022-05:
# To generate a report file listing all fixed CVEs detected from R2022-05
mvn org.talend.ci:builder-maven-plugin:8.0.3:detectCVE
-Dgeneration.type=local
-Dlicense.path=/home/talend/talend_studio/license
-Dproduct.path=/home/talend/talend_studio/commandline/Talend-Studio-YYYYMMDD_1234-V8.0.3/
<!-- This parameter is only supported and needed for users with Talend Studio 8.0.1 R2024-04 or lower
-Dtalend.studio.p2.base=https://update.talend.com/Studio/8/base -->
-Dtalend.studio.p2.update=https://update.talend.com/Studio/8/updates/R2022-05
-DfromVersion=R2022-05
-DcveReportFilePath=/home/talend/talend_studio/CI/cvereport.csv
-s /home/talend/talend_studio/maven_user_settings.xmlDid this page help you?
If you find any issues with this page or its content – a typo, a missing step, or a technical error – let us know how we can improve!
