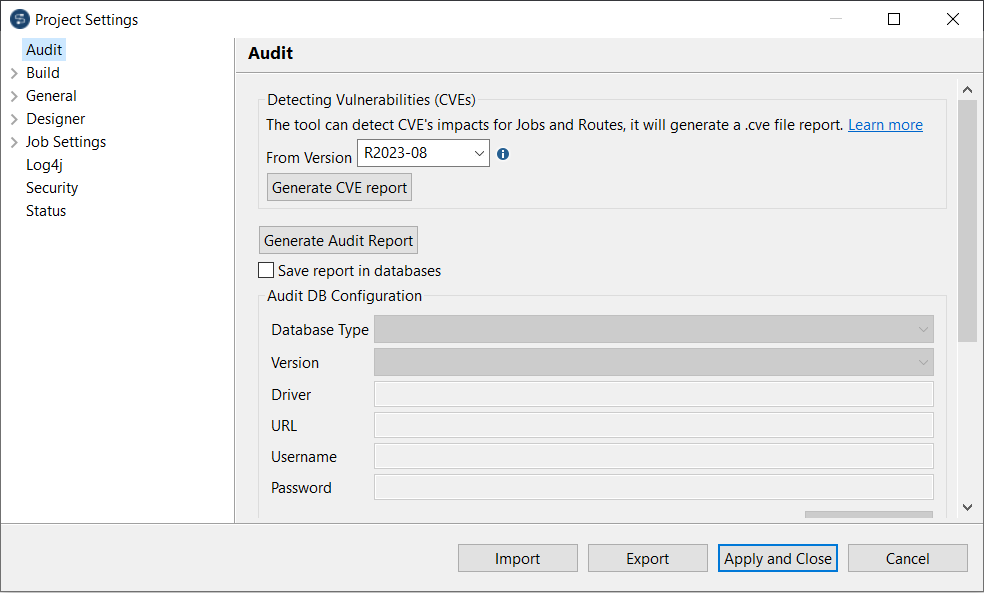
| Status |
Can be:
- Upgraded: The vulnerability has been
fixed by upgrading the library to a new version
- Removed: The vulnerability has been
fixed by removing the library from the
component/distribution/studio plugin dependencies
|
| Fix Version |
The update version when the CVE has been fixed. Example:
R2022-03
|
| Project Name |
Name of the project impacted by the Common Vulnerabilities and
Exposures. Example: LOCAL_PROJECT
|
| Item type |
Type of the artifact impacted by the Common Vulnerabilities and
Exposures. Example: PROCESS
|
| Item ID |
Identifier of the artifact impacted by the Common Vulnerabilities
and Exposures. Example:
_GXOmQFizEeiOq-rLS_Z-8g
|
| Item Name |
Display name of the artifact impacted by the Common
Vulnerabilities and Exposures. Example:
MyVeryComplexJob
|
| GAV with CVE |
The Maven Group, Artifact, Version (GAV) of the JAR file that has
unsolved vulnerabilities. Example:
org.apache.logging.log4j:log4j-core:2.13.2
|
| GAV with CVE mitigated |
The Maven Group, Artifact, Version (GAV) of the JAR file that has
fixed vulnerabilities. Example:
org.apache.logging.log4j:log4j-core:2.17.1
|
| UsedByTalendComponent |
Can be:
- True: The GAV with CVE has been fixed in
the listed components but is still used by Talend Studio somewhere else.
- False: The GAV with CVE has been
completely removed from the Talend Studio component dependencies.
|
| CVE-ID |
Identifier of the Common Vulnerabilities and Exposures. If not
available, you will get CVE-NOT_DISCLOSED. Example:
CVE-2021-44228
|
| CVSS |
The CVSS (Common Vulnerability Scoring System) score for rating
the severity of security vulnerabilities in software. It can be
between 0.0 and 10.0, with
10.0 being the most severe. For more information
about CVSS, see https://nvd.nist.gov/vuln-metrics/cvss. |
| Component Names |
Name of the component impacted by the Common Vulnerabilities and
Exposures. It can be the technical name used for code generation, or
it can be studio if it impacts the whole Talend Studio. |
| Comment |
Additional comments. |