Accessing Secure Services Using Talend Studio and Talend Runtime
SSL is the standard security technology used to establish an encrypted link between a web server and a browser (client). Using SSL ensures the encryption of sensitive information sent over the internet so that it can only be understood by the intended recipient. SSL encryption can be used to simply encrypt the data pipeline, or to perform Client/Server authentication. Client/Server authentication is an approach that aims to prevent man-in-the-middle attack by ensuring that either the Client or the Server authenticates the other, or that they both authenticate each other. This is Mutual SSL.
REST and SOAP web services can leverage SSL with the https protocol to encrypt the pipeline between the client and server. It is easy to configure SSL to access services securely in Talend from both Talend Studio and Talend Runtime.
Authentication and authorization using certificates for external services
It is very common to build data services that consume data from other services in Talend. In the following example, you will convert the SSL certificate of the service you want to call to Java KeyStore (JKS).
- It can be provided by the WebService Provider
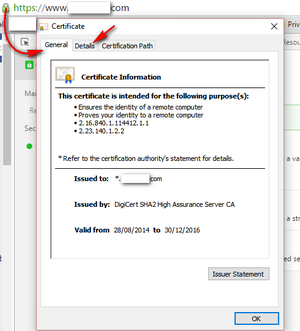
- You can download the SSL certificate by calling the web service in a browser (by trying to read the WSDL in a browser, for example).
The Client Authentication certificate can only be provided by the calling client, you, in this case, or you can provide your certificate to the WebService Provider to store in its trust. In that case, both SSL and Client certificates are provided by the latter.
When you open a secure location through https, you can always inspect the details of the certificate used to encrypt the communication.