Securing access to Talend Change Data Capture
This chapter deals with security in Talend Change Data Capture: more particularly how to handle security in the Manager, in order to limit or provide accesses according to the user profiles.
About this task
You can secure the access not only to a Talend Change Data Capture source machine but also to certain environments. As Talend Change Data Capture security is completely distinct from the intrinsic security of the source machine, the user profiles defined are specific to Talend Change Data Capture.
Information noteNote:
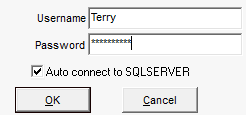
Talend Change Data Capture's profiles and passwords are case-sensitive: uppercase and lowercase characters
are taken into account (e.g. "Terry" is different from "terry").
Procedure
Did this page help you?
If you find any issues with this page or its content – a typo, a missing step, or a technical error – let us know how we can improve!