Manage User Group Assignment
Users may be assigned to one or more groups, as defined in user group administration. Each group assigned controls roles assigned.
Native Group Assignment
Native group assignment may be used for all native users. It may also apply to other users (LDAP, OAuth, SAML) when automatic group assignment is not enabled, and thus when those other users are authenticated they will not have their group assignments reset.
In all these cases, any group assignments may be made as in the following steps.
Steps
- Sign in as a user with at least theSecurity Administratorcapability global role assignment
- Go to MANAGE > Users in the banner.
- Select the user from the list.
- If you have not already done so create a new user.
- If you have not already done so create a new group.
- Click the Groups pull-down and choose the selected group to assign to the user.
Example
Sign in as an Administrator.
Go to MANAGE > Users in the top banner.
Select the user to assign groups to, Stu.

Click the Groups pick list and choose the Business Users group.

Click outside the dialog and SAVE.
Explore Further
Define Administrative Users
Administrative users are those who are assigned to a group which is assigned the Global Administrator global role. To create an administrative user.
Steps
- Sign in as a user with at least theApplication Administratorcapability global role assignment
- Go to MANAGE > Users in the banner.
- Select the user from the list.
- If you have not already done so create a new user.
- Assign the role or group to the user.
One may assign more than one group to a given user. In doing so:
- The user then has the union of all security role assignments provided by those groups
- If any of the groups are assigned to a particular configuration
- Then whenever the user first signs in, they are presented with a choice of configurations from the union of all configurations the groups assigned have access to.
- It is possible at this time or subsequent sign-ins to define a default configuration.
- They may change configurations at any time by clicking on the configuration name in the header and select Change Configuration.
- If none of the groups assigned to the user are assigned to a particular configuration
- Then whenever the user first signs in, they are presented with a choice of configurations from the union of all configurations the groups assigned have access to, which is all.
- It is possible at this time or subsequent sign-ins to define a default configuration.
- They may change configurations at any time by clicking on the configuration name in the header and select Change Configuration.
It is common practice with LDAP, OAuth or SAML authentication to take leverage the information maintained about users in those systems, include organizational structure information, etc., and use this information to assign those users automatically on login to particular groups in the repository. In this way, there is no need to assign users to groups manually.
Once you enable automatic group assignment, every user authenticated by the external authority become a user in the system (if not already defined) and is assigned the proper groups each time they login. Thus, these users will lose any previous manual group assignment at the next login.
In some cases, whether using LDAP or other authentication, is to not depend upon these authentication modes to provide proper group assignment. This is because, those systems are managed by other authorities and are generally not maintained in order to group users so that group assignments logically map.
Instead, it is common to simply use the default group assignment, so that by default, any user is given the Guest group when logging the first time or when created. By default, Guest group is assigned to the Published configuration. In this way, one controls the default presentation to new users, and it is based on a controlled default configuration.
Once the user’s true groups and responsibilities are identified, further groups are assigned to the user.
Automated LDAP Group Assignment
The LDAP configuration window offers a second tab for LDAP driven group assignment. In this case, the groups assignments may be associated to predefined LDAP groups or queries. There are two convenience features helping non LDAP experts retrieve/build the group assignments they need:
- The LDAP group data entry allows one to search for groups defined in your LDAP environment and retrieve the exact LDAP query for such groups. This is very useful when planning to use large predefined groups of business users in group assignment.
- The LDAP search filter data entry allows one to automatically build a proper query to create an LDAP based virtual group of users. This is very useful in creating small Administrator groups or temporarily groups for a project.
In order to create queries defining LDAP driven group assignment.
Talend Data Catalog does not support nested groups, only direct group memberships. The reason for this limitation is there is no universal way to support nested groups across all types of LDAP servers. Although there is a specific way for Active Directory, it does not work properly in forests or when the query contains special characters, so it cannot be used this way either.
Steps
- Sign in as a user with at least theApplication Administratorcapability global role assignment
- Go to MANAGE > Users in the banner.
- Select LDAP Authentication from the Authentication type pull-down in the header.
- Click on Authentication in the header and select LDAP.
- Click on the Group Assignment tab.
- Click on the Add icon.
- Enter the following:
- Provide a Name for the query
- Define the group you wish to associate with users in the query
To assign groups by group name:
- Click on the Browse icon in the Group entry
- Enter a group name in the LDAP system or search text
- Select the Distinguished Name for that group
To specify a search filter and include individual users
- Specify a Search Root like: CN=company,CN=Users,DC=company,DC=local
- Click on the Browse icon in the
 Search Filter entry and select users in that filter.
Search Filter entry and select users in that filter.
To specify a search filter and exclude individual users, you may
- Specify a Search Root: CN=company,CN=Users,DC=company,DC=local
- Use the following syntax: (&(!(sAMAccountName=username1))(!(sAMAccountName=username)))
- Click OK.
Please keep in mind, when you create the first LDAP query for group assignment, you are now switching from native (manually managed) group assignment to LDAP driven (automatic) group assignment for all LDAP users. Any LDAP user will lose any previous native group assignment at the next login.
Similarly, when deleting the last LDAP query for group assignment, you are now switching from LDAP driven (automatic) group assignment, to native (manually managed) group assignment. Any LDAP user will now be only associated to the "Guest" group, until more groups are manually granted to that user.
Automated OAuth Group Assignment
See the details in OAuth Authentication.
In order to support automatic group assignment, specify in the Attribute Mapping tab the corresponding attribute for the security group in Talend Data Catalog . If the attribute group in an OAuth user account information is to be mapped to the security group, the Attribute Mapping tab should look like this:

In this case, if the user account information for user John has a field called group , Talend Data Catalog will use the value of the field group, e.g. "Business user", as the security group assignment for the user John.
The user account information is returned from the OAuth server to Talend Data Catalog after the OAuth server validates an access token upon a login request.
You may also map individual values assigned to the OAuth attribute that maps to the Groups in Talend Data Catalog .
Please keep in mind, when you populate an OAuth attribute for group assignment, you are now switching from native (manually managed) group assignment to OAuth driven (automatic) group assignment for all OAuth users. Any OAuth user will lose any previous native group assignment at the next login.
Similarly, when deleting the last OAuth attribute for group assignment, you are now switching from OAuth driven (automatic) group assignment, to native (manually managed) group assignment. Any OAuth user will now be only associated to the "Guest" group, until more groups are manually granted to that user.
Steps
- Sign in as a user with at least theApplication Administratorcapability global role assignment
- Go to MANAGE > Users in the banner.
- Click ConfigureAuthentication.
- Go to the Group Mappings tab.
- Click the Add Assignment action icon.
Example
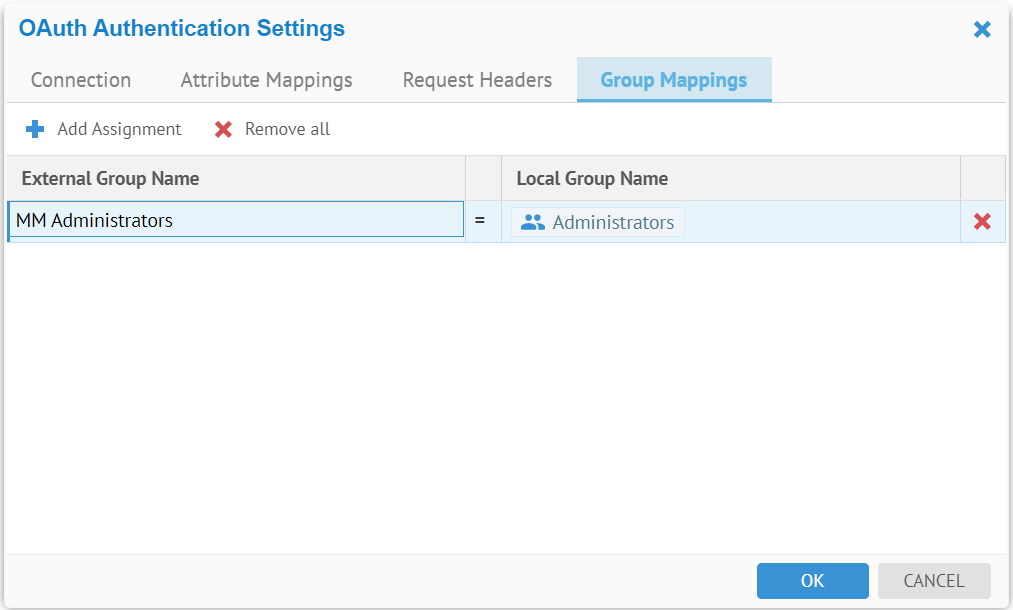
The wildcard (“%”) may be used when configuring group mappings. The % matches zero or more characters.
Automated SAML Group Assignment
See the details in SAML Authentication.
Did this page help you?
If you find any issues with this page or its content – a typo, a missing step, or a technical error – let us know how we can improve!
